V7 ikev2+NAT穿越
1. 组网
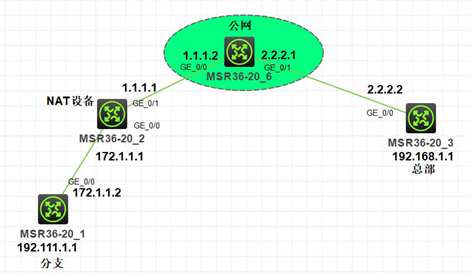
2.需求
MSR1是分支设备,位于NAT设备之后,MSR3是总部,有固定ip地址,现需两设备之间使用IkeV2建立ipsec VPN实现互通。
3.关键配置
分支MSR1:
#
interface LoopBack0
ip address 192.111.1.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 172.1.1.2 255.255.255.252
ipsec apply policy g0/0_ikev2
#
ip route-static 0.0.0.0 0 172.1.1.1
#
acl advanced 3999
rule 0 permit ip source 192.111.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
ipsec transform-set 1
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy g0/0_ikev2 1 isakmp
transform-set 1
security acl 3999
remote-address 2.2.2.2
ikev2-profile 1
#
ikev2 keychain 1
peer msr3
address 2.2.2.2 255.255.255.252
identity address 2.2.2.2
pre-shared-key ciphertext $c$3$zoDTGak1HenDZbFIpZC1MGibxeVHCw==
#
ikev2 profile 1
authentication-method local pre-share
authentication-method remote pre-share
keychain 1
identity local fqdn msr1
match remote identity address 2.2.2.2 255.255.255.252
#
Return
总部MSR3:
#
interface LoopBack0
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.2 255.255.255.252
nat outbound 3888
ipsec apply policy g0/0_ikev2
#
ip route-static 0.0.0.0 0 2.2.2.1
#
acl advanced 3888
rule 0 deny ip source 192.168.1.0 0.0.0.255 destination 192.111.1.0 0.0.0.255
rule 5 permit ip
#
acl advanced 3999
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.111.1.0 0.0.0.255
#
ipsec transform-set 1
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy g0/0_ikev2 1 isakmp
transform-set 1
security acl 3999
remote-address 1.1.1.1
ikev2-profile 1
#
ikev2 keychain 1
peer msr1
address 1.1.1.1 255.255.255.252
identity address 1.1.1.1 //NAT设备的公网地址
pre-shared-key ciphertext $c$3$zoDTGak1HenDZbFIpZC1MGibxeVHCw==
#
ikev2 profile 1
authentication-method local pre-share
authentication-method remote pre-share
keychain 1
match remote identity fqdn msr1
#
Return
或者总部MSR3配置为模板模式:
#
ipsec policy-template g0/0_ikev2 1
transform-set 1
security acl 3999
remote-address 1.1.1.1
ikev2-profile 1
#
ipsec policy g0/0_ikev2 1 isakmp template g0/0_ikev2
#
4.测试
MSR1侧带源pingMS3侧
ping -a 192.111.1.1 192.168.1.1
Ping 192.168.1.1 (192.168.1.1) from 192.111.1.1: 56 data bytes, press CTRL_C to break
Request time out
56 bytes from 192.168.1.1: icmp_seq=1 ttl=255 time=3.000 ms
56 bytes from 192.168.1.1: icmp_seq=2 ttl=255 time=2.000 ms
56 bytes from 192.168.1.1: icmp_seq=3 ttl=255 time=2.000 ms
56 bytes from 192.168.1.1: icmp_seq=4 ttl=255 time=2.000 ms
--- Ping statistics for 192.168.1.1 ---
5 packet(s) transmitted, 4 packet(s) received, 20.0% packet loss
round-trip min/avg/max/std-dev = 2.000/2.250/3.000/0.433 ms
%Jun 22 21:01:35:211 2020 H3C PING/6/PING_STATISTICS: Ping statistics for 192.168.1.1: 5 packet(s) transmitted, 4 packet(s) received, 20.0% packet loss, round-trip min/avg/max/std-dev = 2.000/2.250/3.000/0.433 ms.
MSR1侧:
dis ikev2 sa
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
1 172.1.1.2/4500 2.2.2.2/4500 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: g0/0_ikev2
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1420
Tunnel:
local address: 172.1.1.2
remote address: 2.2.2.2
Flow:
sour addr: 192.111.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.168.1.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3342881310 (0xc740521e)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3588
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 1090629045 (0x4101adb5)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3588
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: Y
Status: Active
MSR3侧:
[H3C]dis ikev2 sa
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
1 2.2.2.2/500 1.1.1.1/1 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
[H3C]dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: g0/0_ikev2
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1412
Tunnel:
local address: 2.2.2.2
remote address: 1.1.1.1
Flow:
sour addr: 192.168.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.111.1.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1090629045 (0x4101adb5)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/2337
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 3342881310 (0xc740521e)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/2337
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: Y
Status: Active
MSR3(模板模式)
[H3C]dis ikev2 sa
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
2 2.2.2.2/500 1.1.1.1/2 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
[H3C]dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: g0/0_ikev2
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1412
Tunnel:
local address: 2.2.2.2
remote address: 1.1.1.1
Flow:
sour addr: 192.168.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.111.1.1/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1116909757 (0x4292b0bd)
Connection ID: 12884901889
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3509
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 2335293618 (0x8b31c0b2)
Connection ID: 12884901888
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3509
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: Y
Status: Active