GRE over ipsec VPN实现多分支互访
1、组网
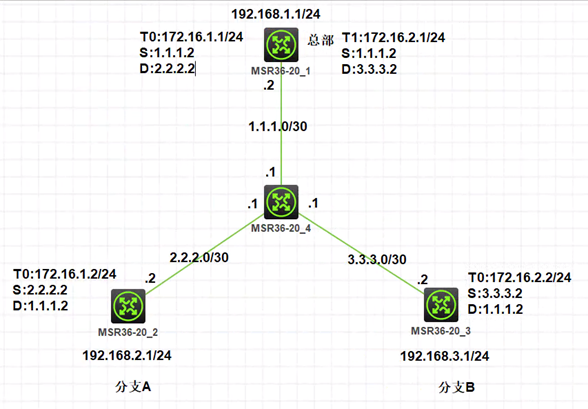
2、需求
建立GRE over ipsec vpn实现各分支和总部之间互通,并且各分支之间也能通过总部访问。总部是固定ip地址,分支IP地址不固定,并且分支A、B处无人值守且分支无主动自动访问总部的业务运行,所以为了防止分支设备断电重启后无法主动建立隧道,需要通过NQA来实现设备断电重启后自动触发隧道建立。
3、配置思路
由于各分支和总部之间建立的是GRE over ipsec VPN,ipsec保护是GRE流量,所以要实现多分支和总部之间互访,只需要将分支访问总部或者别的分支的流量送到GRE tunnel接口进行GRE封装,然后被ipsec保护由ipsec隧道来传输至总部,在总部由ipsec 解封装后再送到GRE 对应的tunnel接口解封装。(如果是访问别的分支的流量,会在总部再匹配静态路由,又送到对应的tunnel接口进行封装走ipsec 隧道到达对应的分支)
4、关键配置
总部:
#
sysname Headquarters
#
interface LoopBack0
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 1.1.1.2 255.255.255.252
//GRE报文不会做NAT,所以此处NAT处不用deny ipsec感兴趣流
nat outbound
ipsec apply policy test
#
interface Tunnel0 mode gre
description toBrabchA
ip address 172.16.1.1 255.255.255.0
source 1.1.1.2
destination 2.2.2.2
#
interface Tunnel1 mode gre
description toBrabchB
ip address 172.16.2.1 255.255.255.0
source 1.1.1.2
destination 3.3.3.2
#
ip route-static 0.0.0.0 0 1.1.1.1
ip route-static 192.168.2.0 24 tunnel0
ip route-static 192.168.3.0 24 tunnel1
#
acl advanced 3000
description toBranchA
rule 0 permit ip source 1.1.1.2 0.0.0.0 destination 2.2.2.2 0.0.0.0
#
acl advanced 3001
description toBranchB
rule 0 permit ip source 1.1.1.2 0.0.0.0 destination 3.3.3.2 0.0.0.0
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template branchA 1
transform-set 1
security acl 3000
ike-profile branchA
#
ipsec policy-template branchB 1
transform-set 1
security acl 3001
ike-profile branchB
#
ipsec policy test 1 isakmp template branchA
#
ipsec policy test 2 isakmp template branchB
#
ike profile branchA
keychain branchA
exchange-mode aggressive
local-identity fqdn headquarters
match remote identity fqdn branchA
#
ike profile branchB
keychain branchB
exchange-mode aggressive
local-identity fqdn headquarters
match remote identity fqdn branchB
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain branchA
match local address 1.1.1.2
pre-shared-key hostname branchA key cipher $c$3$nng95cm/zlG3ghvIRim5saZ3bMEhoJD+Ow==
#
ike keychain branchB
match local address 1.1.1.2
pre-shared-key hostname branchB key cipher $c$3$Rl2okdkTYNBEYWd32X25LOWYkYo5YCcrgw==
#
分支A:
#
sysname branchA
#
nqa entry admin test
type icmp-echo
destination ip 1.1.1.2
frequency 5000
history-record enable
history-record number 10
probe count 10
probe timeout 500
source ip 2.2.2.2
#
nqa schedule admin test start-time now lifetime forever
#
interface LoopBack0
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 2.2.2.2 255.255.255.252
nat outbound
ipsec apply policy 1
#
interface Tunnel0 mode gre
ip address 172.16.1.2 255.255.255.0
source 2.2.2.2
destination 1.1.1.2
#
ip route-static 0.0.0.0 0 2.2.2.1
ip route-static 192.168.1.0 24 Tunnel0
ip route-static 192.168.3.0 24 Tunnel0
#
acl advanced 3000
rule 0 permit ip source 2.2.2.2 0.0.0.0 destination 1.1.1.2 0.0.0.0
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3000
remote-address 1.1.1.2
ike-profile 1
#
ike dpd interval 10 on-demand
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn branchA
match remote identity fqdn headquarters
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain 1
pre-shared-key address 1.1.1.2 255.255.255.0 key cipher $c$3$5QlYyBFEZTju/oTPut9zgP5JNpmVleBIbA==
#
分支B:
#
sysname branchB
#
nqa entry admin test
type icmp-echo
destination ip 1.1.1.2
frequency 5000
history-record enable
history-record number 10
probe count 10
probe timeout 500
source ip 3.3.3.2
#
nqa schedule admin test start-time now lifetime forever
#
interface LoopBack0
ip address 192.168.3.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 3.3.3.2 255.255.255.252
nat outbound
ipsec apply policy 1
#
interface Tunnel0 mode gre
ip address 172.16.1.3 255.255.255.0
source 3.3.3.2
destination 1.1.1.2
#
ip route-static 0.0.0.0 0 3.3.3.1
ip route-static 192.168.1.0 24 Tunnel0
ip route-static 192.168.2.0 24 Tunnel0
#
acl advanced 3000
rule 0 permit ip source 3.3.3.2 0.0.0.0 destination 1.1.1.2 0.0.0.0
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3000
remote-address 1.1.1.2
ike-profile 1
#
ike dpd interval 10 on-demand
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn branchB
match remote identity fqdn headquarters
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain 1
pre-shared-key address 1.1.1.2 255.255.255.0 key cipher $c$3$5QlYyBFEZTju/oTPut9zgP5JNpmVleBIbA==
#
5、测试
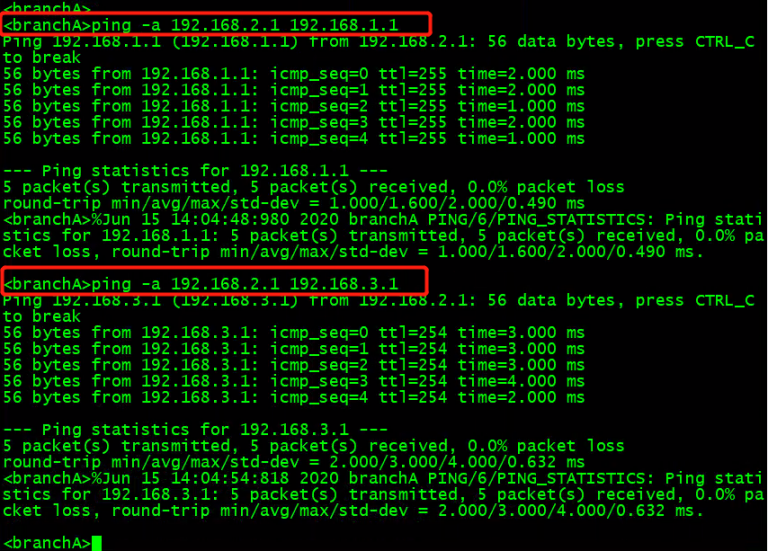
分支A侧可以ping通总部和分支B
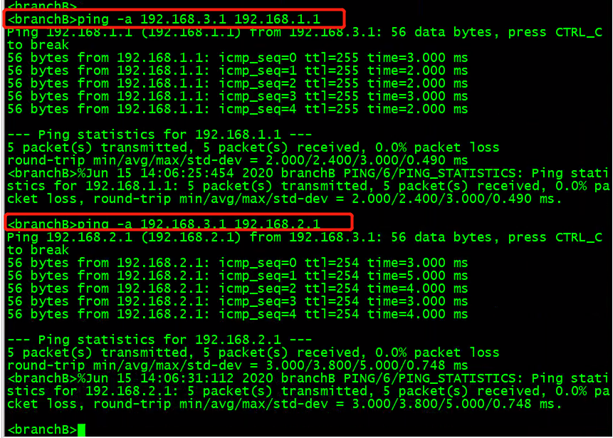
分支B侧可以ping通总部和分支A
在总部侧查看ike sa 和ipsec sa
<Headquarters>dis ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
1 2.2.2.2 RD IPsec
2 3.3.3.2 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
<Headquarters>dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: test
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 1.1.1.2
remote address: 2.2.2.2
Flow:
sour addr: 1.1.1.2/255.255.255.255 port: 0 protocol: ip
dest addr: 2.2.2.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3870699250 (0xe6b62ef2)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843142/3365
Max received sequence-number: 430
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3823032807 (0xe3ded9e7)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843142/3365
Max sent sequence-number: 430
UDP encapsulation used for NAT traversal: N
Status: Active
-----------------------------
IPsec policy: test
Sequence number: 2
Mode: Template
-----------------------------
Tunnel id: 1
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 1.1.1.2
remote address: 3.3.3.2
Flow:
sour addr: 1.1.1.2/255.255.255.255 port: 0 protocol: ip
dest addr: 3.3.3.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3360931740 (0xc853bf9c)
Connection ID: 4294967298
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843138/3366
Max received sequence-number: 460
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 1888065202 (0x708996b2)
Connection ID: 4294967299
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843138/3366
Max sent sequence-number: 460
UDP encapsulation used for NAT traversal: N
Status: Active
在分支A侧查看ike sa 和ipsec sa相关信息
<branchA>dis ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
1 1.1.1.2 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
<branchA>dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: 1
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 2.2.2.2
remote address: 1.1.1.2
Flow:
sour addr: 2.2.2.2/255.255.255.255 port: 0 protocol: ip
dest addr: 1.1.1.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3823032807 (0xe3ded9e7)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843081/3156
Max received sequence-number: 895
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3870699250 (0xe6b62ef2)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843081/3156
Max sent sequence-number: 895
UDP encapsulation used for NAT traversal: N
Status: Active
在分支B侧查看ike sa 和ipsec sa相关信息
<branchB>dis ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
1 1.1.1.2 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
<branchB>dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/0
-------------------------------
-----------------------------
IPsec policy: 1
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 3.3.3.2
remote address: 1.1.1.2
Flow:
sour addr: 3.3.3.2/255.255.255.255 port: 0 protocol: ip
dest addr: 1.1.1.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1888065202 (0x708996b2)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843029/2961
Max received sequence-number: 1285
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3360931740 (0xc853bf9c)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843029/2961
Max sent sequence-number: 1285
UDP encapsulation used for NAT traversal: N
Status: Active
在总部开启debug GRE all和debug ip packet,然后在分支A分别访问总部和分支B,收集debug信息分析一下报文在总部的解封装然后又封装的过程。
[branchA]ping -c 1 -a 192.168.2.1 192.168.1.1
//收到ESP封装的ipsec报文
<Headquarters>*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 160, pktid = 10759, offset = 0, ttl = 254, protocol = 50,
checksum = 35870, s = 2.2.2.2, d = 1.1.1.2
prompt: Receiving IP packet.
//进行ipsec解封装,解封装之后为GRE报文
*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 108, pktid = 10758, offset = 0, ttl = 255, protocol = 47,
checksum = 35670, s = 2.2.2.2, d = 1.1.1.2
prompt: Receiving IP packet.
//送到GRE tunnel0接口进行GRE解封装
*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
Delivering, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 108, pktid = 10758, offset = 0, ttl = 255, protocol = 47,
checksum = 35670, s = 2.2.2.2, d = 1.1.1.2
prompt: IP packet is delivering up.
*Jun 15 12:42:35:746 2020 Headquarters GRE/7/packet:
Tunnel0 packet: Before de-encapsulation,
2.2.2.2->1.1.1.2 (length = 108)
*Jun 15 12:42:35:746 2020 Headquarters GRE/7/packet:
Tunnel0 packet: After de-encapsulation,
192.168.2.1->192.168.1.1 (length = 84)
*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = Tunnel0, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 10757, offset = 0, ttl = 255, protocol = 1,
checksum = 3409, s = 192.168.2.1, d = 192.168.1.1
prompt: Receiving IP packet.
*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
Delivering, interface = Tunnel0, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 10757, offset = 0, ttl = 255, protocol = 1,
checksum = 3409, s = 192.168.2.1, d = 192.168.1.1
prompt: IP packet is delivering up.
//对设备回应的报文继续进行GRE封装
*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
Sending, interface = Tunnel0, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 10757, offset = 0, ttl = 255, protocol = 1,
checksum = 3409, s = 192.168.1.1, d = 192.168.2.1
prompt: Sending the packet from local at Tunnel0.
*Jun 15 12:42:35:746 2020 Headquarters GRE/7/packet:
Tunnel0 packet: Before encapsulation according to adjacency table,
192.168.1.1->192.168.2.1 (length = 84)
*Jun 15 12:42:35:746 2020 Headquarters GRE/7/packet:
Tunnel0 packet: After encapsulation,
1.1.1.2->2.2.2.2 (length = 108)
*Jun 15 12:42:35:746 2020 Headquarters IPFW/7/IPFW_PACKET:
//GRE封装完成之后从外网接口从ipsec隧道转发
Sending, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 160, pktid = 10715, offset = 0, ttl = 255, protocol = 50,
checksum = 35658, s = 1.1.1.2, d = 2.2.2.2
prompt: Sending the packet from local at GigabitEthernet0/0.
[branchA]ping -c 1 -a 192.168.2.1 192.168.3.1
//如下的解封装、封装过程与上面类似,不在赘述。
<Headquarters>
//收到ESP封装的ipsec报文
*Jun 15 14:49:10:944 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 160, pktid = 8947, offset = 0, ttl = 254, protocol = 50,
checksum = 37682, s = 2.2.2.2, d = 1.1.1.2
prompt: Receiving IP packet.
//进行ipsec解封装,解封装之后为GRE报文
*Jun 15 14:49:10:944 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 108, pktid = 8946, offset = 0, ttl = 255, protocol = 47,
checksum = 37482, s = 2.2.2.2, d = 1.1.1.2
prompt: Receiving IP packet.
//送到GRE tunnel0接口进行GRE解封装
*Jun 15 14:49:10:944 2020 Headquarters IPFW/7/IPFW_PACKET:
Delivering, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 108, pktid = 8946, offset = 0, ttl = 255, protocol = 47,
checksum = 37482, s = 2.2.2.2, d = 1.1.1.2
prompt: IP packet is delivering up.
*Jun 15 14:49:10:944 2020 Headquarters GRE/7/packet:
Tunnel0 packet: Before de-encapsulation,
2.2.2.2->1.1.1.2 (length = 108)
*Jun 15 14:49:10:944 2020 Headquarters GRE/7/packet:
Tunnel0 packet: After de-encapsulation,
192.168.2.1->192.168.3.1 (length = 84)
*Jun 15 14:49:10:944 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = Tunnel0, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 8945, offset = 0, ttl = 255, protocol = 1,
checksum = 4709, s = 192.168.2.1, d = 192.168.3.1
prompt: Receiving IP packet.
//根据静态路由将分支A访问分支B的报文又送到tunnel1接口进行GRE封装
*Jun 15 14:49:10:944 2020 Headquarters IPFW/7/IPFW_PACKET:
Sending, interface = Tunnel1, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 8945, offset = 0, ttl = 254, protocol = 1,
checksum = 4965, s = 192.168.2.1, d = 192.168.3.1
prompt: Sending the packet from Tunnel0 at Tunnel1.
*Jun 15 14:49:10:944 2020 Headquarters GRE/7/packet:
Tunnel1 packet: Before encapsulation according to adjacency table,
192.168.2.1->192.168.3.1 (length = 84)
*Jun 15 14:49:10:944 2020 Headquarters GRE/7/packet:
Tunnel1 packet: After encapsulation,
1.1.1.2->3.3.3.2 (length = 108)
*Jun 15 14:49:10:945 2020 Headquarters IPFW/7/IPFW_PACKET:
//GRE封装完成之后从外网接口从ipsec隧道转发至分支B
Sending, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 160, pktid = 9356, offset = 0, ttl = 255, protocol = 50,
checksum = 36504, s = 1.1.1.2, d = 3.3.3.2
prompt: Sending the packet from local at GigabitEthernet0/0.
//收到从分支B返回的回应
*Jun 15 14:49:10:946 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 160, pktid = 9816, offset = 0, ttl = 254, protocol = 50,
checksum = 36300, s = 3.3.3.2, d = 1.1.1.2
prompt: Receiving IP packet.
//进行ipsec解封装,解封装之后为GRE报文
*Jun 15 14:49:10:946 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 108, pktid = 9815, offset = 0, ttl = 255, protocol = 47,
checksum = 36100, s = 3.3.3.2, d = 1.1.1.2
prompt: Receiving IP packet.
//送到GRE tunnel1接口进行GRE解封装
*Jun 15 14:49:10:946 2020 Headquarters IPFW/7/IPFW_PACKET:
Delivering, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 108, pktid = 9815, offset = 0, ttl = 255, protocol = 47,
checksum = 36100, s = 3.3.3.2, d = 1.1.1.2
prompt: IP packet is delivering up.
*Jun 15 14:49:10:946 2020 Headquarters GRE/7/packet:
Tunnel1 packet: Before de-encapsulation,
3.3.3.2->1.1.1.2 (length = 108)
*Jun 15 14:49:10:946 2020 Headquarters GRE/7/packet:
Tunnel1 packet: After de-encapsulation,
192.168.3.1->192.168.2.1 (length = 84)
*Jun 15 14:49:10:946 2020 Headquarters IPFW/7/IPFW_PACKET:
Receiving, interface = Tunnel1, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 8945, offset = 0, ttl = 255, protocol = 1,
checksum = 4709, s = 192.168.3.1, d = 192.168.2.1
prompt: Receiving IP packet.
//tunnel1解封装完成根据静态路由又送到tunnel0接口进行GRE封装
*Jun 15 14:49:10:946 2020 Headquarters IPFW/7/IPFW_PACKET:
Sending, interface = Tunnel0, version = 4, headlen = 20, tos = 0,
pktlen = 84, pktid = 8945, offset = 0, ttl = 254, protocol = 1,
checksum = 4965, s = 192.168.3.1, d = 192.168.2.1
prompt: Sending the packet from Tunnel1 at Tunnel0.
*Jun 15 14:49:10:946 2020 Headquarters GRE/7/packet:
Tunnel0 packet: Before encapsulation according to adjacency table,
192.168.3.1->192.168.2.1 (length = 84)
*Jun 15 14:49:10:946 2020 Headquarters GRE/7/packet:
Tunnel0 packet: After encapsulation,
1.1.1.2->2.2.2.2 (length = 108)
*Jun 15 14:49:10:946 2020 Headquarters IPFW/7/IPFW_PACKET:
//GRE封装完成之后从外网接口从ipsec隧道转发至分支A
Sending, interface = GigabitEthernet0/0, version = 4, headlen = 20, tos = 0,
pktlen = 160, pktid = 9359, offset = 0, ttl = 255, protocol = 50,
checksum = 37014, s = 1.1.1.2, d = 2.2.2.2
prompt: Sending the packet from local at GigabitEthernet0/0.